CVE Research
The research portion of any project is critical. It’s a time to immerse yourself into the relevant research literature in order to define a problem that is both relevant and tractable.

Photo by Steve Halama on Unsplash
This section describes a method to identify and collect relevant CVEs and related information for a selected platform and software component. In this way, CVEs (being both relevant and tractable) provide a practical method to study reported vulnerabilities.
Table of Contents
Platform Dependence
The series of steps within these articles, at a high level, are platform independent. However, the platform choice will have several implications as to environment setup and tools used for analysis. In addition, the security update process is unique per platform and a high level understanding of the process will be necessary to accomplish patch diffing. Discovering how to get system binaries and patched versions of those same binaries will vary. This article follows a Windows path, while also providing a high level concepts applicable across platforms.
Identify CVEs
Security researchers and enthusiasts leverage CVEs as a means to talk about and reference vulnerabilities, at least in so much the fact that there are always new blog posts, github POCs and conference talks about various vulnerabilities with CVEs attached to them. For our purposes, we will be using the CVEs as the starting point in our research. Hoping to eventually transform a CVE into a map to comprehension and discovery. Before we get too far though, we need to understand what CVEs are and how we can leverage them.
CVEs Defined
The Common Vulnerability and Exposures (CVE) is a list of particular instances (specific CVE Identifiers) of reported vulnerabilities maintained by MITRE. The goal of the CVE project is to “Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities”.
A CVE identifier (aka “CVE-IDs”, and “CVEs”) at the time of this writing is defined as:
[CVE prefix + Year + Arbitrary Digits]
Examples include:
- CVE-2020-1048
- CVE-2017-11201
Each CVE contains:
- CVE Identifier - to uniquely identify the vulnerability
- Brief Description
- to provide an understanding of the vulnerability
- Including at least one of the following:
- Vulnerability Type - (RCE,EoP,etc)
- Root Cause
- Impact
- References - a publicly available external reference
Review the CVE Glossary for further details.
Finding CVEs
The easiest method to find CVEs is to go to the source. From there, search for a particular CVE ID or keywords like “Windows Print Spooler” or “Chrome Use After Free””. This list provides the short description and some external reference that might be useful.
Sample Result Table for CVE-2020-1048
| CVE-ID | CVE-2020-1048 |
|---|---|
| Description | An elevation of privilege vulnerability exists when the Windows Print Spooler service improperly allows arbitrary writing to the file system, aka ‘Windows Print Spooler Elevation of Privilege Vulnerability’. This CVE ID is unique from CVE-2020-1070. |
| References | MISC:http://packetstormsecurity.com/files/158222/Windows-Print-Spooler-Privilege-Escalation.html MISC:http://packetstormsecurity.com/files/159217/Microsoft-Spooler-Local-Privilege-Elevation.html MISC:https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1048 |
| Assigning CNA | Microsoft Corporation |
| Date Record Created | 20191104 |
Often, the references only provide shallow information, similar to the short description provided in the CVE link itself. Leveraging the CVE list a more of a ‘fact of’ list, it’s best then to go search for the CVE ID directly and find related blogs which provide more depth. If no blogs exist, which is often the case, there is still hope in patch analysis, but it is a much steeper hill to climb.
List of other good sources:
- Reddit - r/netsec
- Project Zero
- Github
- Twitter (and Tweetdeck)
Finding CVEs of Interest
Finding CVEs of interest is subjective. Certain vulnerability classes might be of interest to a researcher because of familiarity or personal preference. Some objective reasons to consider are:
- availability - whether or not enough information is available to get started. When a new bug class or high profile vulnerability is disclosed, there are often several blog posts and articles detailing the specifics of the vulnerability.
- goals - depth of breadth? broadening horizons or laser focusing on a specific vulnerability class? or mapping out a specific software/system component?
The path followed for CVE analysis in this course is influenced by recent availability of several Windows Print Spooler CVEs and related reports.
CVE Topical Searches
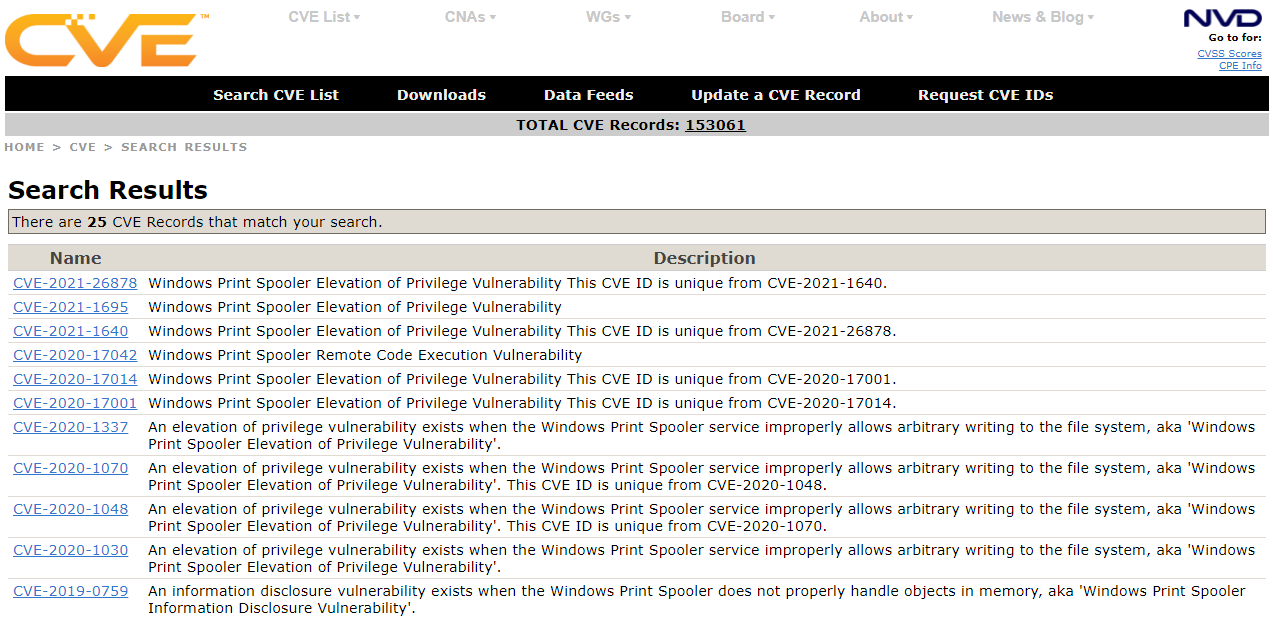
Searching for CVEs is trivial. Head on over to Mitre’s page https://cve.mitre.org. For example. Searching for “Windows Print Spooler” reveals the following table: https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=windows+print+spooler
From the list the following CVEs will be analyzed to walk us down the street of CVE analysis and patch diffing.
| Name | Description |
|---|---|
| CVE-2020-17001 | Windows Print Spooler Elevation of Privilege Vulnerability This CVE ID is unique from CVE-2020-17014. |
| CVE-2020-1337 | An elevation of privilege vulnerability exists when the Windows Print Spooler service improperly allows arbitrary writing to the file system, aka ‘Windows Print Spooler Elevation of Privilege Vulnerability’. |
| CVE-2020-1048 | An elevation of privilege vulnerability exists when the Windows Print Spooler service improperly allows arbitrary writing to the file system, aka ‘Windows Print Spooler Elevation of Privilege Vulnerability’. This CVE ID is unique from CVE-2020-1070. |
| CVE-2020-1030 | An elevation of privilege vulnerability exists when the Windows Print Spooler service improperly allows arbitrary writing to the file system, aka ‘Windows Print Spooler Elevation of Privilege Vulnerability’. |
| CVE-2010-2729 | The Print Spooler service in Microsoft Windows XP SP2 and SP3, Windows Server 2003 SP2, Windows Vista SP1 and SP2, Windows Server 2008 Gold, SP2, and R2, and Windows 7, when printer sharing is enabled, does not properly validate spooler access permissions, which allows remote attackers to create files in a system directory, and consequently execute arbitrary code, by sending a crafted print request over RPC, as exploited in the wild in September 2010, aka “Print Spooler Service Impersonation Vulnerability.” |
Ready to get started
Now that you have list, you can start your journey for understanding. To dig a little deeper, we will move onto the next section detailing CVE analysis on the Windows Print Spooler CVEs listed above.
CVE North Stars Map
graph TD;
classDef current fill:#00cc66;
A1:::current;
A1[CVE Research] --> A[CVE-2020-1048];
A1 --> B[CVE-2020-1337];
A1 --> C[CVE-2020-17001];
A1 --> D[CVE-2010-2729];
A1 --> E[CVE-2020-1030];